 The team on the last day
The team on the last day
So, some time earlier this year we made second place at the Boston Key Party
CTF. The BKP is one of seven CTF events this year where the winner qualified
for DEF CON CTF. The one who came in first had already qualified at that point,
which meant we got the spot. The DEF CON CTF is the big CTF event of the
year, and one of the bigger events at the (in)famous DEF CON hacking conference
in Las Vegas. H*ck yeah road trip to Vegas!
The CTF happened early August, and by the time I finally got to write this blog
post, other teams had published great writeups for almost all challenges. So
unlike other CTF-related posts, this one’s gonna be a travel report for our
casual readers rather than a writeup for the techies. There won’t even be code,
I promise!
One of the first impressions of DEF CON was the line of people at the entrance.
The evening before the first conference day at around 2am, we were wandering
around the hotel and met a flock of people (like, 50) camping in front of the
entrance.
 <figcaption>DEF CON Badges</figcaption>
We thought those guys were crazy, until we saw the line the next day. After we
got our bag full of badges (very awesome badges I might add) from Duchess, just
walking by the line took us minutes, and we didn’t even have to cover the
part outside where people were waiting in line around the pools. Did I mention
Vegas is in the middle of the flippin’ desert and it’s 38 degrees average
outside? With 16k visitors this year, the DEF CON is a huge conference.
Unfortunately, we weren’t able to see much of the conference itself really,
since we were occupied with the CTF almost 100% of the time.
<figcaption>DEF CON Badges</figcaption>
We thought those guys were crazy, until we saw the line the next day. After we
got our bag full of badges (very awesome badges I might add) from Duchess, just
walking by the line took us minutes, and we didn’t even have to cover the
part outside where people were waiting in line around the pools. Did I mention
Vegas is in the middle of the flippin’ desert and it’s 38 degrees average
outside? With 16k visitors this year, the DEF CON is a huge conference.
Unfortunately, we weren’t able to see much of the conference itself really,
since we were occupied with the CTF almost 100% of the time.
Anyways we spent the day before the CTF buying groceries, and the evening doing
last minute preparations.
 <figcaption>Last Minute Preparations</figcaption>
Because “free Wifi” is apparently not something Vegas hotels do, we occupied
the first free bit of conference area we could find. An hour later, at 10pm
sharp, we were kicked out because the room was closing. In fact, every room was
closing, it was end of conference day, show’s over, everybody get out. So we
spent the rest of the evening doing more preparations on the floor. Fun times.
Luckily, spq had already planned out most of our infrastructure beforehand, so
there wasn’t too much left to do.
<figcaption>Last Minute Preparations</figcaption>
Because “free Wifi” is apparently not something Vegas hotels do, we occupied
the first free bit of conference area we could find. An hour later, at 10pm
sharp, we were kicked out because the room was closing. In fact, every room was
closing, it was end of conference day, show’s over, everybody get out. So we
spent the rest of the evening doing more preparations on the floor. Fun times.
Luckily, spq had already planned out most of our infrastructure beforehand, so
there wasn’t too much left to do.
The next day at 9am, the CTF room was opened for the teams. Each of the twenty
teams had their own table with the team name for display on a neat banner, one
power socket, and one cat5 lan cable. We got our network infrastructure set up
without a hitch (“What do you mean, where’s the power supply for the switch?! I
thought you had it!
 <figcaption>The CTF Area</figcaption>
Ok the switch is 9V, maybe this 5V one will work…”), and at 10am it was finally
showtime. The announcers loved saying “Attention teams!”, and their first
announcement was “Attention teams! Powershell access has now been enabled!”
We had talked to some players from other teams the day before, and one of the
topics of discussion was which architecture the CTF would run on. DEF CON CTF
has traditionally favored non-mainstream architectures and operating systems
(ie, not Linux x86-64), and the possibility of a Windows-based CTF had been a
running gag for a while. Luckily, they weren’t serious about that part and we
got ssh to our ARM based ODROID-U2 vulnbox shortly after.
<figcaption>The CTF Area</figcaption>
Ok the switch is 9V, maybe this 5V one will work…”), and at 10am it was finally
showtime. The announcers loved saying “Attention teams!”, and their first
announcement was “Attention teams! Powershell access has now been enabled!”
We had talked to some players from other teams the day before, and one of the
topics of discussion was which architecture the CTF would run on. DEF CON CTF
has traditionally favored non-mainstream architectures and operating systems
(ie, not Linux x86-64), and the possibility of a Windows-based CTF had been a
running gag for a while. Luckily, they weren’t serious about that part and we
got ssh to our ARM based ODROID-U2 vulnbox shortly after.
The following two days and a half went by in a blur. We spent our time hacking
away at the challenges, doing half-automated scans of pcap files for leaked
flags and exploits from other teams, patching our services accordingly or
replaying the attacks.
 <figcaption>Banner, ODroid and Badge</figcaption>
The challenges were a text-based space economy simulator “eliza”, a
webserver-type service “wdub” which later on got its own scripting language
“yodawg”, a constraint solver “justify”, an imap service imaginatively called
“imap”, and finally a hardware challenge “badger”, which was a radio chat
service running on an emulated MSP architecture on an FPGA, running on another
badge style piece of hardware.
<figcaption>Banner, ODroid and Badge</figcaption>
The challenges were a text-based space economy simulator “eliza”, a
webserver-type service “wdub” which later on got its own scripting language
“yodawg”, a constraint solver “justify”, an imap service imaginatively called
“imap”, and finally a hardware challenge “badger”, which was a radio chat
service running on an emulated MSP architecture on an FPGA, running on another
badge style piece of hardware.
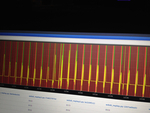 Exploit statistics screenshot
Exploit statistics screenshot
The competition was fierce, to say the least. When the “justify” service was
released on the second day, it took PPP only about half an hour to come up with
a working exploit (here’s a writeup), which was crazy considering it took us
more than an hour and a half to replicate their attack and score some flags
with it. There was a pretty animation of the teams’ attacks and captured flags
running on a big screen most of the time, here’s a replay from around the
time PPP unleashed their justify exploit.
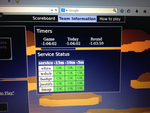 Service overview
Service overview
So I should say something about our performance. I think we did alright all
things considered. We made mistakes, but also discovered new room for
improvement. Firstly, our reverse engineering speed was severely hampered by
lack of an ARM decompiler, which we later learned most teams had - one team
even bought one during the CTF. What was worse though was that over the course
of the entire first day, everyone was so caught up in their hacking haze that
none of us realized there was an internal scoreboard where each team could see
the status of their services.
 <figcaption>Our table, first day</figcaption>
This cost us a lot of points, and at the end of the first day we ended up in
18th place out of twenty. We felt like we should be doing better than that in
the scoring, considering we had defended and pwned all services up to that
point, and in reasonable time. Fortunately, after we finally got that piece of
information in a major “it’s in the readme guys” moment some hours into the
second day, we got our game together and by the evening had worked our way up
to 12th place. On the last day, to keep everyone on their toes, the organizers
decided to remove the public scoreboard. This meant we had no idea how well we
were doing, other than some exploit statistics of our own, the final results
were only published almost a week later.
<figcaption>Our table, first day</figcaption>
This cost us a lot of points, and at the end of the first day we ended up in
18th place out of twenty. We felt like we should be doing better than that in
the scoring, considering we had defended and pwned all services up to that
point, and in reasonable time. Fortunately, after we finally got that piece of
information in a major “it’s in the readme guys” moment some hours into the
second day, we got our game together and by the evening had worked our way up
to 12th place. On the last day, to keep everyone on their toes, the organizers
decided to remove the public scoreboard. This meant we had no idea how well we
were doing, other than some exploit statistics of our own, the final results
were only published almost a week later.
 Room full of innocent bystanders
Room full of innocent bystanders
In the end we made a solid 8th place, which isn’t disappointing but not beyond
our wildest dreams either. One thing is certain, we’ll have to pwn harder next
year! There is a lot more I could write but I don’t want to keep rambling for
too long. It was an awesome experience. We’d like to thank Volkswagen for their
support of the team, we would not have been able to play as easily without
them. Spoiler alert, they will be throwing in some goodies for Zeromutarts
2014 as well, so stay tuned for that!